Boost Online Security: A 15-Min Digital Audit with Our Password Generator
Feeling overwhelmed by the constant drumbeat of data breaches and online threats? You're not alone. Many people know they should improve their online security but don't know where to start. What if you could dramatically boost your digital defenses in just 15 minutes? This guide provides a quick, effective digital security audit you can perform right now. Discover your weak points, strengthen them with powerful tools, and gain the peace of mind that comes from knowing your online life is protected.

It's your moment to take control. We'll guide you through simple, actionable steps that can transform your security from vulnerable to resilient. Let's begin building a safer digital future, starting with a powerful online password generator.
Why a Digital Security Audit is Essential for Everyone
A digital security audit isn't just for tech experts or large corporations; it's a fundamental practice for anyone who uses the internet. Think of it as a routine health check-up for your online presence. It helps you identify and fix vulnerabilities before they can be exploited by malicious actors, ensuring your personal information, financial data, and digital identity remain safe.
The Hidden Dangers of Password Reuse and Weak Credentials
The single greatest threat to most online accounts is the use of weak or repeated passwords. When a single website suffers a data breach, cybercriminals add the leaked usernames and passwords to massive lists. They then use automated software to try those same credentials on hundreds of other popular sites, a technique called "credential stuffing." If you've reused your password, a breach on one minor site can lead to the compromise of your email, banking, and social media accounts. This is why weak credentials are a gateway to widespread digital identity theft.
How an Online Security Check & Strong Password Generator Transforms Your Digital Protection
Performing a regular online security check shifts you from a reactive to a proactive mindset. Instead of waiting for a notification that your account has been compromised, you are actively hunting for and eliminating weaknesses. This simple, methodical process empowers you to truly understand your digital footprint and secure it effectively. You'll replace anxiety with confidence, gaining a clear roadmap for robust digital protection and making it easy to secure your accounts.
Your 15-Minute Action Plan: A Step-by-Step Online Security Audit
Ready to get started? Set a timer for 15 minutes and follow these four straightforward steps. This focused plan is designed for maximum impact with minimum time investment, tackling the most critical areas of your personal security first.
Step 1: Inventory Your Key Online Accounts and Digital Footprint
You can't protect what you don't know you have. Take the first five minutes to list your most critical online accounts. Focus on the high-value targets: primary email addresses, online banking and financial portals, and major social media profiles. This quick inventory of your digital footprint creates a priority list, ensuring you secure your most important assets first. Don't worry about being exhaustive; just capture the essentials.
Step 2: Conduct a Thorough Password Audit for Vulnerabilities
Now, look at your list and honestly assess your passwords. Are you using the same or similar passwords across multiple sites? Are any of them simple, like "Password123," or based on personal information like your pet's name or birthday? This is the core of your password audit. Identify every account that uses a weak or reused password. These are your immediate vulnerabilities that need fixing. For each one, your goal is to replace it with a strong, unique password, something a custom password generator can do in seconds.
Step 3: Bolster Defenses by Enabling Two-Factor Authentication (2FA) Everywhere
A strong password is your first line of defense, and two-factor authentication (2FA) is your powerful second line. 2FA requires a second piece of information—usually a code sent to your phone—in addition to your password to log in. This means that even if a criminal steals your password, they still can't access your account. Take five minutes to enable 2FA on all the critical accounts you listed in Step 1. Most services offer this feature in their security settings.
Step 4: Review and Revoke Unused App Permissions & Close Old Accounts
Over time, we grant countless apps and services access to our accounts and data. The final part of your audit is a quick clean-up. Review the app permissions connected to your Google, Apple, and social media accounts. If you no longer use an app, revoke its access. Likewise, if you have old accounts on services you no longer visit, take a moment to close them. Each unused account is a potential security risk waiting to be exploited.
Securing Your Future: Continuous Online Account Protection
Your 15-minute audit is a fantastic start, but true digital security is an ongoing process. The goal is to build habits that keep you protected for the long haul. This means using the right tools and understanding the principles that underpin modern account security.
Generating Unbreakable & Unique Passwords with Ease
The biggest challenge identified in your audit is likely replacing all those weak and reused passwords. Manually creating and remembering dozens of complex passwords is an impossible task. This is where a strong password generator becomes your most valuable ally. A reliable tool allows you to instantly generate long, random, and complex passwords that are virtually impossible for hackers to guess or crack. You can customize the length and include uppercase letters, lowercase letters, numbers, and symbols to meet any site's requirements and generate a password that offers maximum protection.
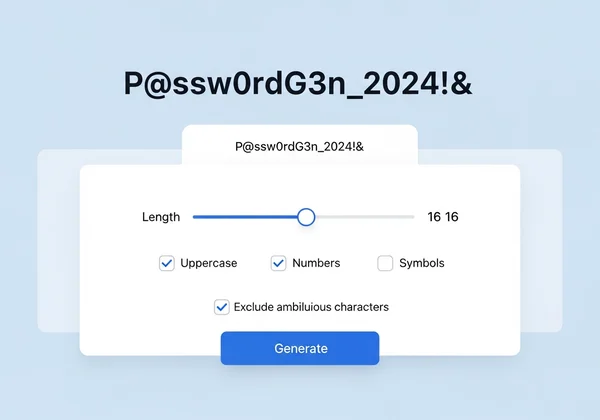
The Unrivaled Security of Client-Side Password Generation
When choosing an online tool, security is paramount. How do you make a password without worrying if the tool itself is safe? The answer lies in client-side password generation. This means the entire process happens locally in your browser on your computer. Your password is never sent over the internet or stored on any server. Our secure password generator is built on this principle of ultimate privacy. The password you create is for your eyes only, giving you the trust and confidence needed to secure your most sensitive accounts.
Leveraging a Password Manager for Seamless Security
Once you've generated all these new, unique passwords, you need a secure place to store them. This is the role of a password manager. These applications act as an encrypted digital vault for all your credentials. You only need to remember one master password to access all your others. Using a password manager in conjunction with a password generator creates a seamless and highly secure workflow, eliminating the temptation to fall back into old, insecure habits.

Your Ongoing Journey to a Secure Online Life
Congratulations! By completing this 15-minute audit, you have taken a monumental step toward securing your digital life. You’ve identified weaknesses, learned about crucial defenses like 2FA, and discovered the tools needed to create a strong foundation of security. Remember that this is a journey, not a destination. Make this audit a quarterly habit to stay ahead of threats.
Continue to empower yourself with the best tools available. Start today by replacing your weakest passwords with credentials created by a secure and trustworthy tool. Visit our free password generator and take the next step toward a safer online experience.
FAQ Section
How often should I perform a digital security audit?
For most people, conducting a quick 15-minute audit every three to six months is an excellent practice. You should also perform an immediate audit if you hear about a data breach at a service you use. Regular check-ins ensure your defenses remain strong against new threats.
What is the most effective way to create a strong, unique password?
The most effective method is to use a trusted random password generator. A good generator creates long, unpredictable strings of characters, including upper and lowercase letters, numbers, and symbols. This randomness is what makes them resistant to brute-force attacks. Aim for a length of 16 characters or more for optimal security.
Are online password generators safe to use for my security audit?
Is my password secure when I use a generator? This is a critical question. The safety of an online password generator depends entirely on its architecture. You should only use tools that operate exclusively on the client-side, like the one found at PasswordGenerator.vip. This guarantees that the passwords you create are never transmitted or stored by the website, ensuring your complete privacy.
How can I manage all my strong and unique passwords generated during an audit?
The best way to manage a large number of unique passwords is with a reputable password manager. These tools securely store and encrypt your credentials, allowing you to access them with a single master password. Many can even automatically fill in login forms for you, combining top-tier security with everyday convenience.