Common Password Attacks: How an Online Password Generator Protects You
Passwords are your frontline defense in today's digital landscape, safeguarding everything from your personal emails to sensitive financial data. Yet, many of us underestimate the persistent and sophisticated threats lurking online. Understanding the common password attacks used by cybercriminals is the first step toward building a robust defense. How do you make a password secure enough to withstand these threats?
Let's break down the most common methods hackers use to compromise accounts. More importantly, it will equip you with a practical defense strategy to protect your digital identity. By the end, you will know exactly how to stop hackers in their tracks, starting with creating truly strong credentials with a reliable online password generator.
Understanding Common Password Attack Methods
Hackers employ a variety of techniques to steal your passwords, ranging from brute force guessing to sophisticated psychological manipulation. Knowing what you're up against is crucial for effective protection. Let's break down the most prevalent attack vectors.
What is a Brute Force Attack?
Imagine a hacker trying to open a combination lock by systematically trying every possible number sequence. That’s the essence of a brute force attack in the digital realm. Attackers use automated software to generate and test millions of password combinations per second against a login portal. These attacks prey on short and simple passwords.
A password like "cat123" could be cracked almost instantly. The longer and more complex your password is, the more combinations a brute force attack must try, making it exponentially more difficult and time-consuming for the attacker. This is why password length is one of the most critical factors in account security.

The Stealth of Dictionary Attacks
A dictionary attack is a more refined version of a brute force attack. Instead of trying random character strings, the software uses a pre-compiled list, or "dictionary," of common words, phrases, and frequently used passwords (like "password" or "qwerty"). These lists often include variations with numbers or symbols appended, such as "Sunshine1!" or "Dragon2024".
This method is highly effective because so many people create passwords based on real words for easier recall. If your password is a common word, even with a few modifications, it remains a prime target for a dictionary attack. True randomness is your best defense against this common hacking technique.
What is Credential Stuffing?
One of the most widespread threats today is credential stuffing. This attack leverages the unfortunate habit of password reuse. It starts when a major website suffers a data breach, and user login credentials (usernames and passwords) are stolen and often shared on the dark web.
Hackers then take these lists and use bots to "stuff" them into the login forms of countless other websites, like banking, email, and e-commerce platforms. The bot automatically tests each username/password pair, hoping the user recycled their credentials. A single breach can lead to a cascade of compromised accounts, making it essential to use a unique password for every single service you use. A secure password generator is an invaluable ally in this fight.
Beyond Cracking: Phishing & Social Engineering
Not all attacks are purely technical; some exploit human psychology. Phishing is a form of social engineering where attackers trick you into voluntarily giving them your password. They might send a deceptive email that appears to be from a legitimate company, like your bank or a service like Netflix.
These emails often create a sense of urgency, claiming your account has been compromised or needs verification. They direct you to a fake login page that looks identical to the real one. When you enter your credentials, they are sent directly to the attacker. Vigilance and skepticism are your best tools against these deceptive tactics.
How to Prevent Password Hacking: Your Defense Strategy
Now that you understand the threats, it's time to build your defense. Protecting your accounts doesn't require being a cybersecurity expert. It simply involves adopting a few fundamental, high-impact habits that can dramatically reduce your vulnerability to attacks.
The Golden Rule: Strong, Unique Passwords
Your first and most powerful line of defense is using a strong, unique password for every online account. But what makes a password strong?
- Length: Aim for a minimum of 16 characters. Longer is always better.
- Complexity: Include a mix of uppercase letters, lowercase letters, numbers, and symbols (e.g., !, @, #, $).
- Randomness: Avoid dictionary words, personal information (like birthdays or names), and predictable patterns.
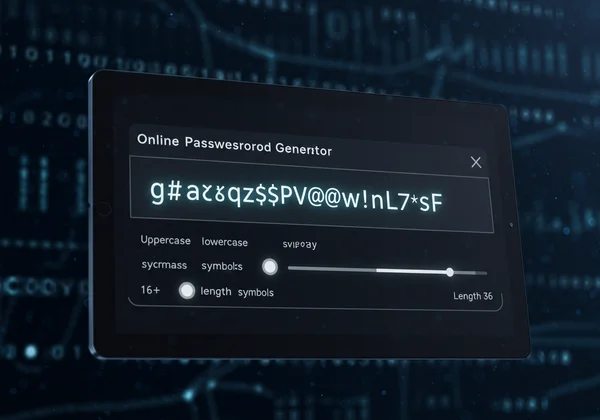
Crafting passwords that meet these criteria is difficult for humans. Our brains naturally gravitate toward patterns. This is where a custom password generator becomes essential. It creates truly random, complex credentials that are nearly impossible for brute force or dictionary attacks to crack.
Adding Layers: The Power of Two-Factor Authentication (2FA)
Think of Two-Factor Authentication (2FA) as a second lock on your digital door. Even if a hacker manages to steal your password, they still can't access your account without a second piece of information. This second factor is typically something only you possess.
Common forms of 2FA include:
- A code sent to your phone via SMS.
- A code generated by an authenticator app (like Google Authenticator or Authy).
- A physical security key (like a YubiKey).
Enabling 2FA wherever possible is one of the single most effective actions you can take to secure your accounts. It provides a critical safety net against compromised passwords.
Simplifying Security: Why You Need a Password Manager
The advice to use a long, random, and unique password for every site seems daunting. How can anyone remember dozens of credentials like "8#qZ$vP@w!nL7*sF"? The answer is: you don't have to. A password manager is a secure, encrypted vault that stores all your login information.
You only need to remember one strong master password to unlock the manager. It can then automatically fill in your credentials on websites and apps. When paired with a tool to generate a password, it creates a seamless workflow: generate a strong password, save it in your manager, and never worry about it again.
Spotting the Traps: Vigilance Against Phishing
Defending against social engineering requires awareness. To avoid falling victim to phishing scams, adopt these habits:
- Inspect the Sender: Always check the sender's email address. Scammers often use addresses that are slightly different from the real one.
- Hover Before You Click: Before clicking any link in an email, hover your mouse over it to see the actual destination URL. If it looks suspicious, don't click.
- Beware of Urgency: Be skeptical of emails that demand immediate action or threaten you with negative consequences.
- Go Directly to the Source: If you're unsure, close the email and navigate to the website directly by typing the address into your browser.
Your Best Defense: Embracing Strong Passwords
The digital landscape is filled with threats, but you are not powerless. By understanding common password attacks like brute force, credential stuffing, and phishing, you can take decisive action to protect yourself. Your primary shield is, and always will be, a strong and unique password for every account.
Don't leave your security to chance or rely on weak, memorable phrases. Take control of your digital safety today. Use a trusted and secure password generator free tool to create powerful, random passwords for all your accounts. It’s a simple, free step that provides an immense boost to your online security.

Your Top Questions on Password Security
How do I create a truly strong password?
A truly strong password combines length, complexity, and randomness. The best practice is to use a dedicated tool to generate it. A strong password should be at least 16 characters long and contain a mix of uppercase letters, lowercase letters, numbers, and symbols. Avoid using personal information or common words, as these are easily guessed by attackers.
What characteristics define a "good" password?
A "good" password is one that is unpredictable and resistant to cracking attempts. Its strength is measured by something called entropy—a measure of its randomness. Instead of trying to create one yourself, the most effective method is to use a reliable random password generator. This ensures the password has no predictable patterns that hacking software can exploit.
Are online password generators safe to use?
This is a critical question. The safety of an online password generator depends entirely on how it works. You should only use generators that perform all calculations on your device (client-side) and do not send any information to a server. Our online password generator guarantees your privacy with a client-side only approach. The passwords you create are generated in your browser and are never seen, stored, or transmitted by us, making our trusted tool a truly safe choice.
How long should my passwords be for optimal security?
For optimal security, cybersecurity experts now recommend passwords be a minimum of 16 characters long. While 12 was once a common recommendation, increasing computing power has made longer passwords necessary to defend against modern brute force attacks. Using a password generator makes creating and managing these longer, more complex passwords effortless.