How to Create a Strong Password with 2FA: The Ultimate Security Guide
In today's digital world, a strong, unique password is the first lock on your digital door. You diligently avoid "password123" and use a mix of characters, which is a fantastic first step. But with cyber threats becoming more sophisticated, even the best lock needs a deadbolt. That deadbolt is two-factor authentication (2FA). Many people hesitate, thinking it’s complicated or a hassle. How do you make a password truly secure? This guide will demystify what is two-factor authentication, showing you how this simple, powerful tool can elevate your account security in just a few minutes. Before adding that second lock, ensure the first is unbreakable. A strong password generator that creates your password locally on your device provides the secure foundation you need.
What is Two-Factor Authentication (2FA)?
Two-factor authentication is a security process that requires you to provide two different authentication factors to verify your identity. Think of it as needing two keys to open a single door. Simply put, it adds a second, crucial step to your login process, making it much harder for unauthorized individuals to gain access to your accounts, even if they manage to steal your password. This method dramatically increases the security of your online identity.

How 2FA Provides a Second Layer of Security
The core principle of 2FA relies on combining two out of three possible types of credentials:
- Something you know: This is your password or PIN.
- Something you have: This is a physical item, like your smartphone or a dedicated hardware key.
- Something you are: This refers to biometrics, like your fingerprint or face scan.
Standard logins only use the first factor. 2FA adds the second factor, typically "something you have." So, when you log in, you first enter your password. Then, the service prompts you for a second piece of information—usually a temporary code sent to your phone or generated by an app. Without access to your physical device, a hacker with your password is still locked out. This principle of account security is fundamental to protecting your data.
Understanding the Difference: 2FA vs. MFA
You might also hear the term Multi-Factor Authentication (MFA). The concept is simple: 2FA is a specific type of MFA. While 2FA always involves two factors, MFA can involve two or more. For most personal use cases, 2FA provides a massive security upgrade and is the most common standard. Understanding MFA security helps you recognize that 2FA is part of a broader security strategy recommended by experts worldwide, including institutions like the National Institute of Standards and Technology (NIST).
Why Your Strong Password Needs a Partner
Even the most complex password can be compromised. Massive data breach events happen regularly, exposing millions of usernames and passwords. Hackers can also use sophisticated phishing attacks to trick you into revealing your credentials. If you reuse that password on other sites, all those accounts are now vulnerable.
This is why every account needs a unique password, and your most important accounts need 2FA. A strong password is your first line of defense, but 2FA is the critical backup that protects you when that first line is breached. You can create secure password combinations effortlessly with our tool, which generates them right in your browser without ever storing your data, ensuring your first line of defense is as strong as possible.
Choosing Your 2FA Method: From Good to Best
Not all 2FA methods are created equal. They offer different balances of convenience and security. Understanding your options allows you to choose the right level of protection for your needs, whether you're an everyday user or a security-conscious professional.
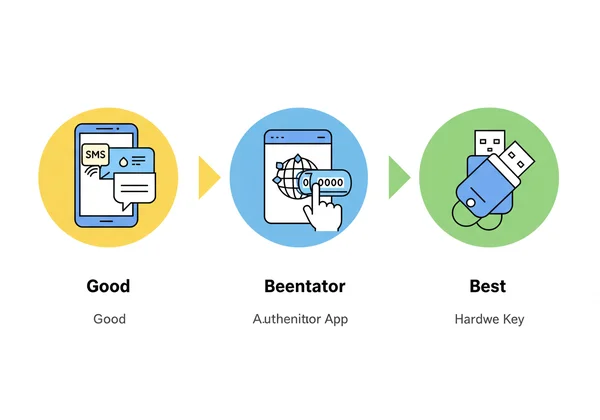
SMS Text Codes: The Convenient Starting Point
This is the most common and accessible form of 2FA. When you log in, the service sends a one-time code to your phone via SMS.
- Pros: It's extremely easy to set up and uses the phone number you already have.
- Cons: It's the least secure method. It is vulnerable to "SIM swapping," a type of attack where a criminal convinces your mobile carrier to transfer your phone number to their own device, allowing them to intercept your codes.
While better than no 2FA at all, it's best to use a more secure method for high-value accounts like email and banking.
Authenticator Apps: The Secure Standard
This method uses a dedicated app on your smartphone (like Google Authenticator, Microsoft Authenticator, or Authy) to generate time-based one-time passwords (TOTP). These codes refresh every 30-60 seconds.
- Pros: Much more secure than SMS because the codes are generated offline on your device and are not vulnerable to SIM swapping.
- Cons: Requires you to install a separate app.
For the vast majority of users, an authenticator app is the gold standard, offering an excellent balance of high security and user convenience.
Hardware Keys: The Ultimate in MFA Security
A hardware key (or security key) is a small physical device, often resembling a USB drive (like a YubiKey or Google Titan Key), that you plug into your computer or tap on your phone to approve a login.
- Pros: This is the most secure form of 2FA available today. It is virtually immune to phishing and remote attacks because the physical key must be present to log in.
- Cons: It costs money to purchase the device, and you need to carry it with you.
This method is highly recommended for protecting extremely sensitive accounts, such as financial platforms, cryptocurrency exchanges, or primary email accounts for business owners and IT professionals.
How to Set Up 2FA: A Step-by-Step Guide
Enabling 2FA is easier than you think. Most major online services have streamlined the process into a few simple steps. Here’s a general guide to get you started.
Enabling 2FA on Your Google & Email Accounts
Your primary email account is the key to your digital kingdom, so secure it first. For a Google account:
- Go to your Google Account settings and navigate to the "Security" tab.
- Look for the "2-Step Verification" option and click on it.
- Follow the on-screen prompts. You will be asked to verify your password and choose your second factor.
- We highly recommend choosing "Authenticator App" and scanning the provided QR code with your chosen app.
- Google will ask you to enter a code from the app to confirm it's working correctly.
The process is very similar for other email providers like Outlook and Yahoo. Always start by finding the "Security" or "Account Security" section in your settings.
Securing Your Social Media (Facebook, Instagram, X)
Your social media accounts contain personal information that can be valuable to attackers. To enable 2FA:
- Go to the "Settings" or "Settings and Privacy" section of the app.
- Find the "Security" or "Password and Security" menu.
- Look for the "Two-Factor Authentication" option.
- Choose your preferred method (Authenticator App is recommended) and follow the setup instructions.
Saving Your Backup Codes Safely
During the 2FA setup process, nearly every service will provide you with a set of one-time-use backup codes. This is a crucial step. These codes are your lifeline if you lose your phone or 2FA device. Treat them like a spare house key:

- Do not store them as a screenshot on your phone or in an unsecured file on your computer.
- Do print them out and store them in a safe place, like a locked drawer or a safe.
- Alternatively, save them inside a trusted and secure password manager.
Your Next Step to a More Secure Digital Life
Combining a strong, unique password with two-factor authentication is the modern standard for effective online safety. 2FA is not a complicated feature for tech experts; it's an accessible and essential tool for everyone. It acts as a powerful shield, protecting your most valuable digital assets from ever-present threats.
Your journey to better security starts with a solid foundation. Before you enable 2FA across your accounts, ensure your first line of defense is impenetrable. Use a trusted online password generator that works entirely in your browser. Our tool creates strong, random passwords on your device, ensuring they are never sent to or stored on our servers. Then, lock down those accounts with the power of two-factor authentication.
Frequently Asked Questions About 2FA
What happens if I lose my phone or 2FA device?
This is why saving your backup codes is so important. When you set up 2FA, you are given a list of codes that you can use to access your account if your primary device is lost or broken. Use one of these codes to log in, and then immediately reset your 2FA with your new device.
Is 2FA completely foolproof against hackers?
No security measure is 100% foolproof, but 2FA raises the bar for attackers immensely. While extremely sophisticated, targeted phishing attacks can theoretically bypass some forms of 2FA, it protects you from the vast majority of common threats like password theft from data breaches. Using an authenticator app or a hardware key makes you a much harder target.
Do I really need 2FA for every online account?
Ideally, yes. However, you should prioritize your most critical accounts first. This includes your primary email, online banking, social media, and any password managers. For less critical accounts, a unique, strong password may be sufficient. You can get a password generator free of charge to create these unique passwords for all your sites, ensuring every account has a solid defense.