Ultimate Guide: Password Security Best Practices for 2024
In an era where our lives are increasingly intertwined with the digital world, the threat of cyberattacks looms larger than ever. At the heart of your online defense lies a fundamental, yet often underestimated, component: robust password security. What are the most effective password security best practices to safeguard your digital assets in 2024? This ultimate guide aims to be your comprehensive playbook, covering everything from creating uncrackable credentials to vigilant management and leveraging tools like Two-Factor Authentication (2FA) and password managers. Adopting these secure password habits is no longer optional; it's essential. Ready to fortify your digital life? You can start by ensuring you're using a reliable method for creating strong passwords.
Foundation of Security: Creating Uncrackable Passwords
The very first step in any solid password security best practices framework is the creation of strong, difficult-to-guess passwords. This forms the bedrock of your account security. How do you create truly uncrackable passwords?
Recap: Length, Complexity, and Randomness
As we've detailed in our guide to creating truly strong passwords, the core pillars are:
- Length: Aim for a minimum of 12-16 characters, or even longer for critical accounts.
- Complexity: Use a mix of uppercase letters, lowercase letters, numbers, and symbols.
- Randomness: Avoid predictable patterns, dictionary words, or personal information.
The Cardinal Sin: Avoiding Password Reuse at All Costs
One of the most critical secure password habits is ensuring every single online account has its own unique password. Reusing passwords, even strong ones, creates a massive vulnerability. If one site is breached and your reused password is leaked, all other accounts using that same password become instantly compromised.
Crafting Strong, Unique Passwords for Every Account
Manually creating and remembering dozens of strong, unique passwords is a near-impossible task for humans. This is where technology plays a vital role in upholding password hygiene.
Using a Reliable Strong Password Generator
To consistently create passwords that meet the criteria for length, complexity, and randomness, employing a strong password generator is highly recommended. These tools instantly generate robust passwords, eliminating the guesswork and human tendency towards predictable patterns. You can learn how to use our password generator effectively to achieve this.
Smart Storage: Keeping Your Passwords Safe and Accessible
Creating strong passwords is only half the battle; you also need a secure way to store and manage them. This is where a password manager becomes an indispensable tool in your password security best practices arsenal.
Why You Absolutely Need a Password Manager
A password manager is a secure, encrypted application designed to store all your complex, unique passwords. You only need to remember one strong "master password" to unlock your vault of credentials. This allows you to use incredibly strong passwords for all your accounts without the burden of memorizing them. What's the best way to manage passwords? For most, it's a password manager.

Choosing a Reputable Password Manager: Key Features
When selecting a password manager, look for:
- Strong encryption methods (e.g., AES-256).
- Cross-platform availability (desktop, mobile).
- Browser integration for auto-filling credentials.
- A built-in strong password generator.
- Support for 2FA on the manager account itself.
- A good reputation for security and transparency.
Securing Your Master Password: The Key to Your Kingdom
Your master password for the password manager is the most important password you'll have. It must be exceptionally strong and unique – ideally a long, memorable passphrase that you've never used anywhere else. Protect it diligently.
Dangers of Unsafe Storage Methods
Avoid storing passwords in unencrypted spreadsheets, text files, sticky notes, or letting your browser save them without robust master password protection. These methods are highly vulnerable to malware and physical theft, undermining your secure password habits.
Beyond Passwords: The Power of Two-Factor Authentication (2FA)
Even the strongest password can potentially be compromised. That's why Two-Factor Authentication (2FA), also known as multi-factor authentication (MFA), is a non-negotiable layer in modern password security best practices. What is 2FA and why is it so crucial?
What is 2FA and How Does It Work?
2FA adds a second layer of verification beyond just your username and password. After entering your password, you'll be prompted to provide a second piece of evidence to prove your identity. This second factor is typically something you have (like a code from an app or a security key) or something you are (like a fingerprint).
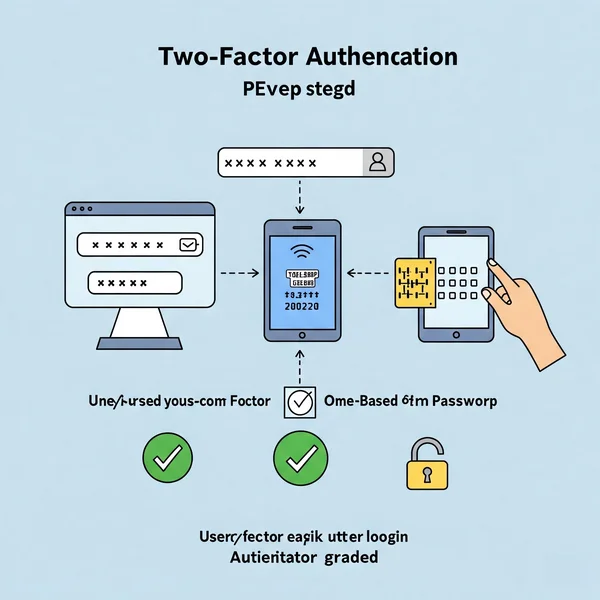
Different Types of 2FA Methods
Common 2FA methods include:
- SMS Codes: A one-time code sent to your phone via text message. (Convenient, but considered less secure than other methods due to SIM swapping risks).
- Authenticator Apps: Apps like Google Authenticator, Authy, or Microsoft Authenticator generate time-based one-time passwords (TOTPs). (More secure than SMS).
- Hardware Security Keys: Physical USB/NFC keys (like YubiKey) that provide a highly secure form of authentication. (Generally the most secure option).
- Biometrics: Fingerprint or facial recognition.
Why 2FA is a Non-Negotiable Security Layer
2FA significantly increases your account security because even if an attacker obtains your password, they still need access to your second factor to log in. This thwarts most automated attacks and many targeted ones.
Enabling 2FA on Your Key Accounts
Prioritize enabling 2FA on all your critical accounts: email, banking, social media, cloud storage, and especially your password manager. Most major services offer 2FA setup options in their security settings.
Vigilant Management: Developing Secure Password Habits
Effective password security best practices involve more than just strong creation and storage; they require ongoing vigilance and good secure password habits. How do you maintain strong password hygiene over time?
Regularly Reviewing Account Security Settings
Periodically check the security settings of your important online accounts. Look for authorized devices, linked applications, and review activity logs if available. Remove any unrecognized access.
The Truth About Password Expiration Policies
For many years, mandatory frequent password changes were common advice. However, current NIST password guidelines (National Institute of Standards and Technology) suggest that if passwords are strong and unique (and ideally protected by 2FA), forcing frequent changes can sometimes lead to users creating weaker, more predictable passwords. The focus has shifted to creating very robust passwords from the start.
Knowing When to Change a Password
You should immediately change your password for an account if:
- The service announces a data breach.
- You suspect your account has been compromised.
- You've accidentally shared your password or clicked on a suspicious link.
- You're logging out of a shared or public computer.
Securely Deleting Old or Unused Accounts
Old, dormant accounts can become security liabilities if their data is breached. If you no longer use an online service, take the time to properly delete your account rather than just abandoning it. This is an important aspect of good password hygiene.
Recognizing and Responding to Password Threats
Part of maintaining secure password habits is being able to recognize and respond to common threats that aim to steal your credentials. What are some common password threats?
Spotting Phishing Scams and Suspicious Emails/Websites
Phishing is a common attack where criminals send fake emails or create fake websites designed to trick you into revealing your login credentials. Be wary of unsolicited emails asking for passwords, links that look suspicious, or websites with incorrect URLs or poor design. Always verify the legitimacy of a site before entering your password.
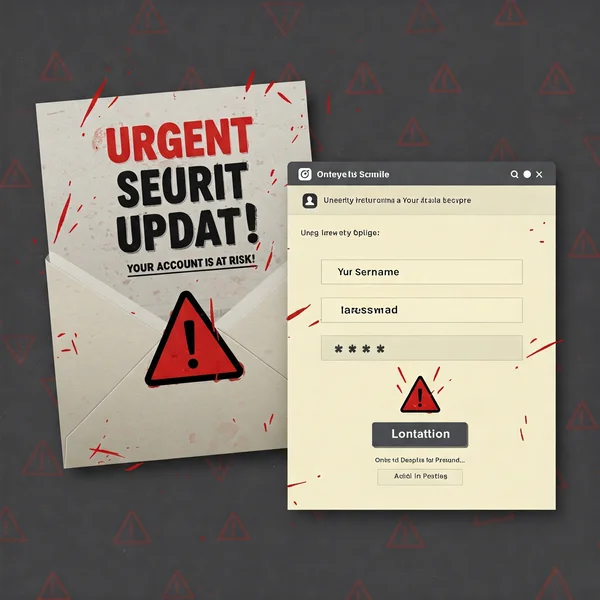
What to Do If You Suspect a Password Breach
If you suspect an account has been compromised:
- Immediately change the password for that account to a new, strong, unique one (use your trusted password generator).
- If you reused that password anywhere else (which you shouldn't!), change it on those accounts too.
- Enable 2FA on the account if it's not already active.
- Review account activity for any unauthorized actions.
- Report the incident to the service provider if necessary.
Using "Have I Been Pwned?" and Similar Services
Services like "Have I Been Pwned?" allow you to check if your email address has appeared in known data breaches. This can alert you to compromised accounts where you should urgently change your password.
The Role of a Strong Password Generator in Best Practices
Throughout this guide, the importance of strong, unique passwords has been a recurring theme. A strong password generator is a fundamental tool that directly supports many of these password security best practices.
Automating Strong, Unique Password Creation
A strong password generator automates the creation of passwords that meet stringent length and complexity requirements, ensuring each one is unique and highly resistant to guessing.
Facilitating Adherence to Length and Complexity Rules
Instead of manually trying to devise complex combinations, a generator does it instantly, making it easy to adhere to best practice recommendations for password construction.

Reducing the Temptation to Create Weak or Reused Passwords
By making strong password creation effortless, a generator helps overcome the human tendency to opt for simpler, weaker, or reused passwords out of convenience. It's a cornerstone of developing secure password habits.
Your Ongoing Commitment to Password Security
Mastering password security best practices isn't a one-time task but an ongoing commitment to protecting your digital identity. By focusing on creating strong, unique passwords, utilizing a reputable password manager, enabling 2FA wherever possible, and cultivating vigilant secure password habits, you can significantly reduce your risk of becoming a victim of cybercrime. Remember, the tools and knowledge are available – it's up to you to use them effectively.
Start strengthening your digital defenses now by applying these best practices. Our password generation tool can help you create the strong, unique passwords you need as a foundational step.
What's your number one password security habit or tip you'd share with others? Let us know in the comments below!
Password Security Best Practices FAQs
Q1: How often should I really change my passwords in 2024?
A: According to current NIST password guidelines, if your password is very strong, unique, and ideally protected by 2FA, mandatory frequent changes (e.g., every 90 days) are no longer broadly recommended. Change passwords primarily if you suspect a compromise or if a service you use announces a breach. Focus on initial strength and uniqueness.
Q2: What are the key NIST password guidelines I should know?
A: Key takeaways from NIST password guidelines include: emphasizing password length over forced complexity (like requiring specific numbers of symbols if the password is long enough), discouraging periodic password changes for strong passwords, and strongly advocating for 2FA. They also recommend checking passwords against breach lists.
Q3: Is it safe to let my browser save my passwords?
A: While convenient, relying solely on browser-based password saving is generally less secure than using a dedicated password manager. Browsers may not offer the same level of encryption or protection for their stored credentials, and if your browser profile is compromised, all saved passwords could be at risk. If you do use it, ensure your browser itself is protected by a strong primary password if that feature is available.
Q4: What's the most important password security tip?
A: It's hard to pick just one, but two are paramount: 1) Use a strong, unique password for every single online account (no reuse!). 2) Enable Two-Factor Authentication (2FA) wherever it's offered. These two practices together provide a massive boost to your account security.
Q5: How can a password generator improve my overall security?
A: A strong password generator is crucial because it helps you easily create passwords that are long, complex, and truly random – characteristics that make them highly resistant to common hacking attempts. It removes the human element of creating weak or predictable passwords and is a cornerstone of good password hygiene. Using a reliable generator is one of the first steps in implementing robust password security best practices.